The need for a trusted timestamp
Identifying date/time for events as they happen is critical. Failing to identify the correct date and time makes the information irrelevant as it reduces its relevance. As an example what if the deed of a car sale doesn’t mention what date it was signed or the birth certificate doesn’t mention what date/time someone was born etc. In simple words putting correct date & time on electronic records / documents is critical for us and this process is called timestamping. During Timestamping the following aspects are key:
- Where is the time taken from and is it trustworthy?
- Can the mentioned time be forged in future?
Where is the time taken from?
Getting time from your watch or mobile can be wrong due to mechanical or technical flaws. A slack of one or two minutes might be OK to mention when submitting your university assignment but critical electronic business transactions will not tolerate this. In the electronic world, time is normally taken from local computer sync with the internet clock. For critical application time is taken from the atomic clock. The Network Time Protocol (NTP) is normally used to synchronize time between two systems.
Protecting Timestamp forgery
In the digital era, placing time on paper is now replaced with adding time on your electronic document e.g. email, word or pdf document. Note that in electronic documents changing content is much easier and less detectable than in the paper based world. One of the most critical parts in timestamping is to ensure any timestamp created can’t be forged in future. Hence digital signatures come to the rescue. The time hence taken and placed on a digital document is also digitally signed. This ensures any change in either the timestamped content or the time can be easily detected. Digital Signature also identifies who created the time hence can be questioned in future about its authority.

How Timestamp server produces timestamps
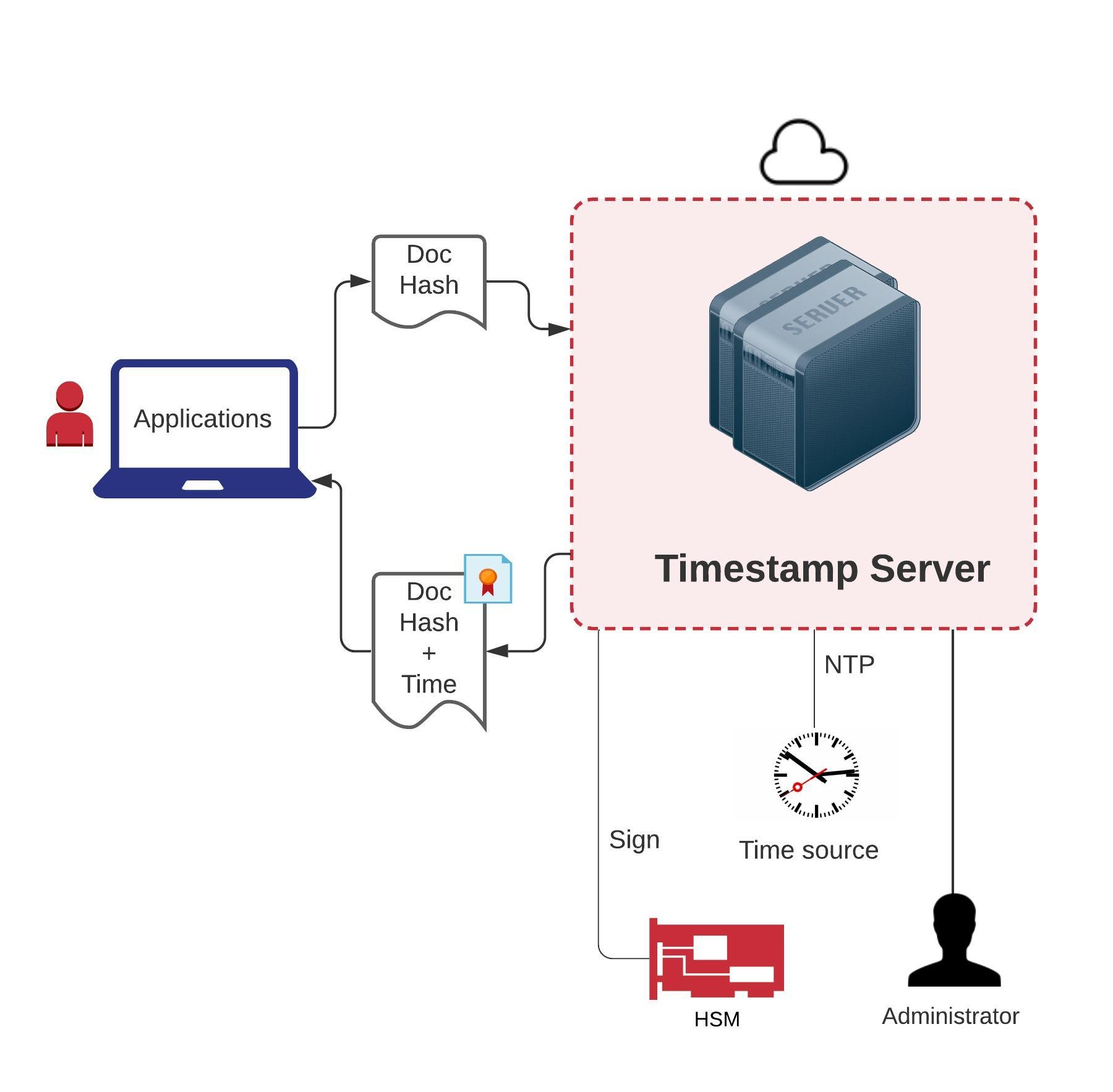
Timestamp servers are normally built as software programs but can also be deployed as a hardware boxes. Timestamp servers take in timestamp requests and generate the timestamp response. The process can be defined as:
- Clients of Timestamp servers are business applications who are signing documents or transactions (xml or json). They process the input document which needs to be time stamped and identifies its hash e.g. SHA-256, form the time stamp request as per RFC 3161 and send it to the Timestamp Server
- The Timestamp server verifies the incoming request as per RFC 3161 standard and create a digitally signed timestamp response which contains:
- The input document hash
- The time at which the response is being created
- Other data like nonce, extensions
- The time source from where Timestamp server gets the time can be:
- Current machine time
- Time from HSM
- Time from external time source over NTP
Timestamping Format
IETF defined RFC 3161 (with few updates in RFC 5816) standard which guides on how to record timestamp inside any electronic content be it XML, Word documents or PDF. Another somewhat similar standard used specifically by Microsoft is called Authenticode. The RFC 3161 timestamp request and response can be summarized as:
Timestamp request and responses are defined in ASN.1 formats.

RFC 3161 Timestamp Request Detailed
TimeStampReq ::= SEQUENCE { version INTEGER { v1(1) }, messageImprint MessageImprint, reqPolicy TSAPolicyId OPTIONAL, nonce INTEGER OPTIONAL, certReq BOOLEAN DEFAULT FALSE, extensions [0] IMPLICIT Extensions OPTIONAL } MessageImprint ::= SEQUENCE { hashAlgorithm AlgorithmIdentifier, hashedMessage OCTET STRING } TSAPolicyId ::= OBJECT IDENTIFIER
Authenticode Request
Microsoft code signing tools utilize the Authenticode standard for timestamping.
TimeStampRequest ::= SEQUENCE { countersignatureType OBJECT IDENTIFIER, attributes Attributes OPTIONAL, content ContentInfo }
Authenticode Response
The time stamp response is a PKCS #7 signed message signed by the time stamp server.
RFC 3161 Timestamp Response Detailed
TimeStampResp ::= SEQUENCE { status PKIStatusInfo, timeStampToken TimeStampToken OPTIONAL } PKIStatusInfo ::= SEQUENCE { status PKIStatus, statusString PKIFreeText OPTIONAL, failInfo PKIFailureInfo OPTIONAL } PKIStatus ::= INTEGER { granted (0), grantedWithMods (1), rejection (2), waiting (3), revocationWarning (4), revocationNotification (5) } PKIFailureInfo ::= BIT STRING { badAlg (0), badRequest (2), badDataFormat (5), timeNotAvailable (14), unacceptedPolicy (15), unacceptedExtension (16), addInfoNotAvailable (17), systemFailure (25) } TimeStampToken ::= ContentInfo -- contentType is id-signedData ([CMS]) -- content is SignedData ([CMS]) TSTInfo ::= SEQUENCE { version INTEGER { v1(1) }, policy TSAPolicyId, messageImprint MessageImprint, serialNumber INTEGER, genTime GeneralizedTime, accuracy Accuracy OPTIONAL, ordering BOOLEAN DEFAULT FALSE, nonce INTEGER OPTIONAL, tsa [0] GeneralName OPTIONAL, extensions [1] IMPLICIT Extensions OPTIONAL }
Applications creating timestamp
Timestamps are now common in many document processing applications when they are digitally signing documents. Some of these are:
- Adobe Acrobat
- Microsoft Word
- OpenSSL & curl
- jarsigner
- SignTool
How to apply a cryptographic timestamp on a pdf using Adobe Acrobat Reader
The free Adobe Acrobat Reader DC allows you to digitally sign PDF documents with timestamps. Here are the steps to create one:
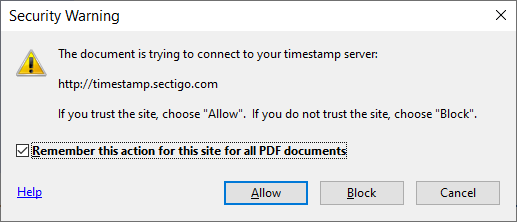
- Ensure you first configure Adobe Acrobat Reader with a timestamp server
- To configure a timestamp server you can pick one from the list of free timestamp servers
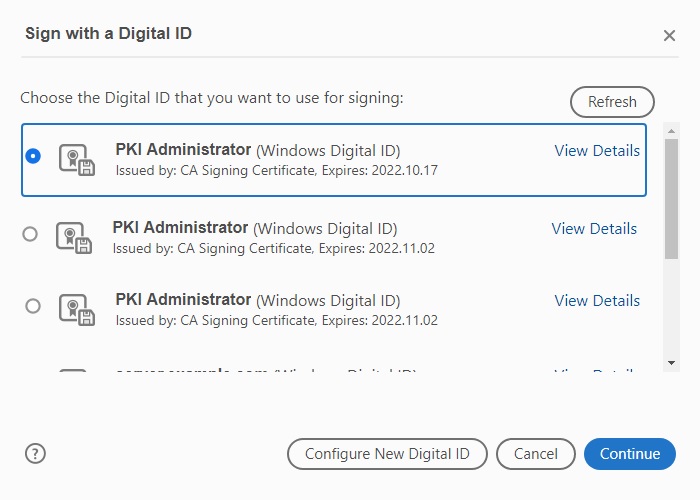
- Once done, create a signature field and choose the signing certificate
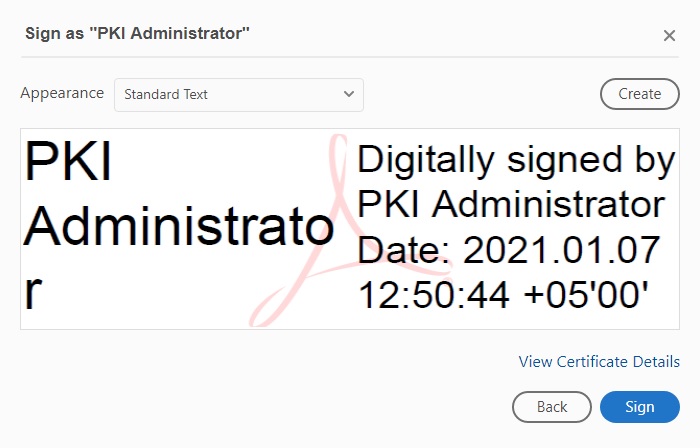
Select the digital signing certificate and press Sign button:
How to apply a cryptographic timestamp on word documents using Microsoft Word
To get step by step actions on creating digital signatures in Microsoft Word click here. By default, creating timestamps during signing is disabled. To enable timestamps in Office 2010 onwards, configure two entries in registries via regedit.
- Change XAdESLevel set to 2
- Set TSALocation set to your timestamp server
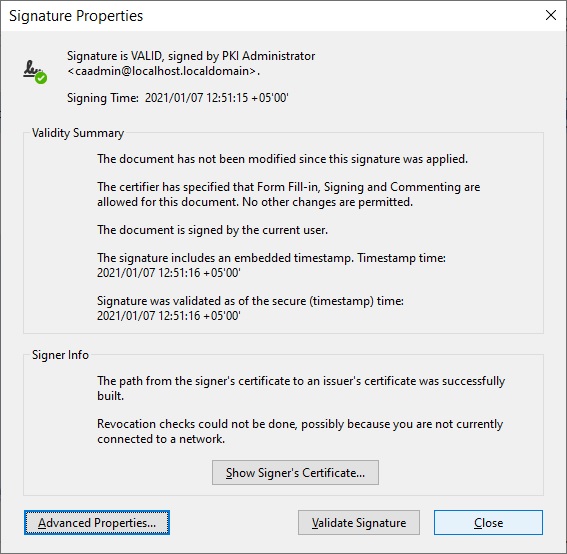
Once done, restart Microsoft Word, create a signature line and sign the document. Note that Microsoft Word 2010 onwards creates XML based digital signatures. On verifying the signature you will see the XAdES-T format which denotes that the digital signature also has an embedded timestamp information.
How to create and send timestamp requests using OpenSSL & Curl
OpenSSL is open source crypto tool to create RFC 3161 based timestamps. Unfortunately you can’t send these via OpenSSL hence you have to rely on Curl. The following command will create timestamp and saves it on hard disk. Windows release for OpenSSL can be found here.
openssl ts -query -sha256 -cert -data C:\\test\\openssl\\timestamp\\hello-world.txt -out C:\\test\\openssl\\timestamp\\tsa_request.ts
Parsing Timestamp Request using OpenSSL
openssl ts -query -in C:\\test\\openssl\\timestamp\\tsa_request.ts -text Using configuration from C:\Program Files\OpenSSL-Win64-111g\bin\cnf\openssl.cnf Version: 1 Hash Algorithm: sha256 Message data: 0000 - b9 4d 27 b9 93 4d 3e 08-a5 2e 52 d7 da 7d ab fa .M'..M>...R..}.. 0010 - c4 84 ef e3 7a 53 80 ee-90 88 f7 ac e2 ef cd e9 ....zS.......... Policy OID: unspecified Nonce: 0x96952486F1BFE380 Certificate required: yes Extensions:
Sending Timestamp Request using curl
curl -H "Content-Type:application/timestamp-query" --data-binary "@C:\\test\\openssl\\timestamp\\tsa_request.ts" http://timestamp.sectigo.com -o "C:\\test\\openssl\\timestamp\\tsa_response.tsr"
Parsing Timestamp Response using OpenSSL
openssl ts -reply -in C:\\test\\openssl\\timestamp\\tsa_response.tsr -text D:\Data\codegic\Software\curl\curl-7.70.0-win64-mingw\curl-7.70.0-win64-mingw\bin>openssl ts -reply -in C:\\test\\openssl\\timestamp\\tsa_response.tsr -text Using configuration from C:\Program Files\OpenSSL-Win64-111g\bin\cnf\openssl.cnf Status info: Status: Granted. Status description: unspecified Failure info: unspecified TST info: Version: 1 Policy OID: 1.3.6.1.4.1.6449.2.1.1 Hash Algorithm: sha256 Message data: 0000 - b9 4d 27 b9 93 4d 3e 08-a5 2e 52 d7 da 7d ab fa .M'..M>...R..}.. 0010 - c4 84 ef e3 7a 53 80 ee-90 88 f7 ac e2 ef cd e9 ....zS.......... Serial number: 0x4F5C6033A07903AA689A0B814FB239F49A8C50F8 Time stamp: Jan 8 17:14:46 2021 GMT Accuracy: unspecified Ordering: no Nonce: 0x96952486F1BFE380 TSA: DirName:/C=GB/ST=Greater Manchester/L=Salford/O=Sectigo Limited/CN=Sectigo RSA Time Stamping Signer #2 Extensions:
How to code sign & add timestamp jar files using jarsigner
jarsigner allows digitally signing (code sign) of jar files and optionally added timestamp information. jarsigner tools comes with JDK (Oracle or OpenJDK both).
Signing jar file
jarsigner -tsa http://localhost:8080/timestamp/tsa -tsapolicyid 1.3.6.1.4.1.4146.4 -tsadigestalg SHA-256 -keystore "C:\signer.p12" -storepass p#34343s2 -signedjar "C:\jar-signing\signed.jar" "C:\jar-signing\totp.jar" ahmad jar signed. The signer certificate will expire on 2023-04-14. The timestamp will expire on 2027-01-31.
Parameter Details
-tsa: Points to the timestamp server url
-tsapolicyid: Mentions the timestamp policy which timestamp server must use
-tsadigestalg: Hashing algorithm used to create the request e.g. SHA-256, SHA-512 etc
-keystore: Keystore file (PKCS#12 file/Java Keystore) used to sign the jar file
-storepass: Password of the keystore
-signedjar: Name of the to be created signed jar file
The last two parameters are the input jar and the signing certificate alias inside the keystore. Ensure that the signing certificate used to sign the jar file is created with Code Signing purpose otherwise a warning will come at signing and verification time.
Verifying signatures on a jar file
jarsigner -verify -verbose "C:\test\jar-signing\signed-jar.jar" s 289 Tue Feb 08 13:05:24 PKT 2022 META-INF/MANIFEST.MF 311 Tue Feb 08 13:05:24 PKT 2022 META-INF/1.SF 7863 Tue Feb 08 13:05:24 PKT 2022 META-INF/1.RSA 0 Thu Sep 17 15:23:48 PKT 2020 META-INF/ 0 Thu Sep 17 15:23:48 PKT 2020 totp/ sm 5501 Thu Sep 17 15:23:48 PKT 2020 totp/Totp.class s = signature was verified m = entry is listed in manifest k = at least one certificate was found in keystore - Signed by "CN=Signing Certificate lkKx" Digest algorithm: SHA-256 Signature algorithm: SHA256withRSA, 2048-bit key Timestamped by "OU=security, O=codegic, CN=soft-key-rsa-2048, C=pk" on Tue Feb 08 08:05:24 UTC 2022 Timestamp digest algorithm: SHA-256 Timestamp signature algorithm: SHA256withRSA, 2048-bit key jar verified. The signer certificate will expire on 2023-04-14. The timestamp will expire on 2027-01-31.
Reference: The jarsigner Command (oracle.com)
How to apply cryptographic timestamps on exe, dll files using SignTool
Windows comes with a built in tool which signs executables and dll file. You may optionally add timestamp and embed it inside the signed binary file.
Digitally signing exe, dll & adding timestamp using SignTool
signtool sign /f C:\test\code-signing\code-signing.pfx /v /debug /p password /tr http://192.168.18.6:8080/timestamp/tsa /fd SHA256 C:\code-signing\tobe-signed.exe
The following certificates were considered: Issued to: Code signing Issued by: Codegic Sub CA Expires: Sat Apr 09 15:50:42 2022 SHA1 hash: 31F50D0975E0CD2397E0EBD44DFF75CF3C85EF82 Issued to: Codegic Sub CA Issued by: Codegic Root CA Expires: Tue Jan 08 19:47:52 2036 SHA1 hash: C0CF2C70F431535DFE8CD06B03C1CAC015E71352 Issued to: Codegic Root CA Issued by: Codegic Root CA Expires: Sun Jan 08 19:47:51 2051 SHA1 hash: B34CFEA1CFFA98043E92BEAC8BD72E7CBDFF4A47 After EKU filter, 3 certs were left. After expiry filter, 3 certs were left. After Private Key filter, 1 certs were left. The following certificate was selected: Issued to: Code signing Issued by: Codegic Sub CA Expires: Sat Apr 09 15:50:42 2022 SHA1 hash: 31F50D0975E0CD2397E0EBD44DFF75CF3C85EF82 The following additional certificates will be attached: Issued to: Codegic Sub CA Issued by: Codegic Root CA Expires: Tue Jan 08 19:47:52 2036 SHA1 hash: C0CF2C70F431535DFE8CD06B03C1CAC015E71352 Done Adding Additional Store Successfully signed: C:\test\code-signing\tobe-signed.exe Number of files successfully Signed: 1 Number of warnings: 0 Number of errors: 0
Parameter Details
/f: Points to the Private Key File (PKCS#12/PFX) or use the /csp and /kc options to specify the CSP and private key container name
/v: Creates a verbose output
/debug: Helps in debugging issues if any
/p: Points to the password incase of a PKCS#12/PFX file
/tr: Points to the timestamp server URL
/fd: Points to the hashing algorithm used in the timestamp request e.g. SHA256, SHA512 etc.
The last parameter points to the binary file to be signed.
Reference: SignTool.exe (Sign Tool) – .NET Framework | Microsoft Docs
Verifying digital signature & timestamp on exe, dll using SignTool
signtool verify /pa C:\code-signing\tobe-signed.exe
File: C:\test\code-signing\tobe-signed.exe Index Algorithm Timestamp ======================================== 0 sha256 RFC3161 Successfully verified: C:\test\code-signing\tobe-signed.exe
FAQ
What is a cryptographic timestamp and why is it important?
A cryptographic timestamp is a secure way to record the date and time of events, ensuring their accuracy and relevance. It’s crucial for electronic records/documents to have correct timestamping to maintain their integrity and authenticity. Timestamping ensures that the mentioned time cannot be forged in the future, providing a reliable reference point for events.
How are cryptographic timestamps produced and verified?
Cryptographic timestamps are generated by timestamp servers, which receive timestamp requests from business applications and create digitally signed timestamp responses. These responses contain information such as the input document hash, the time of the response creation, and other relevant data. The timestamp server retrieves the time from trusted sources, such as the atomic clock or network time protocol (NTP). Verification involves checking the timestamp response for validity, including its status, timestamp signer name, and time accuracy.
I want timestamping to be incorporated in my business workflow, how can Codegic help?
Codegic offers Khatim Timestamp Server provide blazing fast, trusted timestamps with NTP servers. Check more details here.