Try before you buy!
Codegic hosts a free timestamp server allowing developers to quickly integrate & test with their business applications.
Disclaimer: You must not integrate the free timestamp server with your production systems. We provide no SLA with the free timestamp server.
Timestamp Integration Rules
http://pki.codegic.com/codegic-service/timestamp
https://pki.codegic.com/codegic-service/timestamp
Sample Requests
To ease testing, use the following sample timestamp request
Request Type
Parsed via OpenSSL
Response
SHA1
Download File: tsa_request_sha_1.ts
Version: 1 Hash Algorithm: sha1 Message data: 0000 - a9 4a 8f e5 cc b1 9b a6-1c 4c 08 73 d3 91 e9 87 .J.......L.s.... 0010 - 98 2f bb d3 ./.. Policy OID: unspecified Nonce: 0x21B5B7A12C3EE59D Certificate required: yes
Status: Rejected. Status description: unspecified Failure info: transaction not permitted or supported
SHA256
Download File: tsa_request_sha_256.ts
Version: 1 Hash Algorithm: sha256 Message data: 0000 - 9f 86 d0 81 88 4c 7d 65-9a 2f ea a0 c5 5a d0 15 .....L}e./...Z.. 0010 - a3 bf 4f 1b 2b 0b 82 2c-d1 5d 6c 15 b0 f0 0a 08 ..O.+..,.]l..... Policy OID: unspecified Nonce: 0xF7EF6BDB714736AC Certificate required: yes Extensions:
Status: Granted. Status description: unspecified Failure info: unspecified
SHA384
Download File: tsa_request_sha_384.ts
Version: 1 Hash Algorithm: sha384 Message data: 0000 - 76 84 12 32 0f 7b 0a a5-81 2f ce 42 8d c4 70 6b v..2.{.../.B..pk 0010 - 3c ae 50 e0 2a 64 ca a1-6a 78 22 49 bf e8 ef c4 <.P.*d..jx"I.... 0020 - b7 ef 1c cb 12 62 55 d1-96 04 7d fe df 17 a0 a9 .....bU...}..... Policy OID: unspecified Nonce: 0x06AF26598DEA0B1E Certificate required: yes Extensions:
Status: Granted. Status description: unspecified Failure info: unspecified
SHA512
Download File: tsa_request_sha_512.ts
Version: 1 Hash Algorithm: sha512 Message data: 0000 - ee 26 b0 dd 4a f7 e7 49-aa 1a 8e e3 c1 0a e9 92 .&..J..I........ 0010 - 3f 61 89 80 77 2e 47 3f-88 19 a5 d4 94 0e 0d b2 ?a..w.G?........ 0020 - 7a c1 85 f8 a0 e1 d5 f8-4f 88 bc 88 7f d6 7b 14 z.......O.....{. 0030 - 37 32 c3 04 cc 5f a9 ad-8e 6f 57 f5 00 28 a8 ff 72..._...oW..(.. Policy OID: unspecified Nonce: 0xDBFB6C133CB2E52E Certificate required: yes
Status: Granted. Status description: unspecified Failure info: unspecified
SHA512-NoNonce
Download File: tsa_request_sha_512_no_nonce.ts
Version: 1 Hash Algorithm: sha512 Message data: 0000 - ee 26 b0 dd 4a f7 e7 49-aa 1a 8e e3 c1 0a e9 92 .&..J..I........ 0010 - 3f 61 89 80 77 2e 47 3f-88 19 a5 d4 94 0e 0d b2 ?a..w.G?........ 0020 - 7a c1 85 f8 a0 e1 d5 f8-4f 88 bc 88 7f d6 7b 14 z.......O.....{. 0030 - 37 32 c3 04 cc 5f a9 ad-8e 6f 57 f5 00 28 a8 ff 72..._...oW..(.. Policy OID: unspecified Nonce: unspecified Certificate required: yes
Status: Rejected. Status description: unspecified Failure info: transaction not permitted or supported
SHA256-Policy-1.2.2
Download File: tsa_request_sha_256_1.2.2.ts
Version: 1 Hash Algorithm: sha256 Message data: 0000 - 9f 86 d0 81 88 4c 7d 65-9a 2f ea a0 c5 5a d0 15 .....L}e./...Z.. 0010 - a3 bf 4f 1b 2b 0b 82 2c-d1 5d 6c 15 b0 f0 0a 08 ..O.+..,.]l..... Policy OID: 1.2.2 Nonce: 0x802FCC89F75B29A2 Certificate required: yes Extensions:
Status: Granted. Status description: unspecified Failure info: unspecified
SHA256-Policy-1.9.9
Download File: tsa_request_sha_256_1.9.9.ts
Version: 1 Hash Algorithm: sha256 Message data: 0000 - 9f 86 d0 81 88 4c 7d 65-9a 2f ea a0 c5 5a d0 15 .....L}e./...Z.. 0010 - a3 bf 4f 1b 2b 0b 82 2c-d1 5d 6c 15 b0 f0 0a 08 ..O.+..,.]l..... Policy OID: 1.9.9 Nonce: 0x6BEA9567778366A2 Certificate required: yes Extensions:
Status: Rejected. Status description: unspecified Failure info: the requested TSA policy is not supported by the TSA
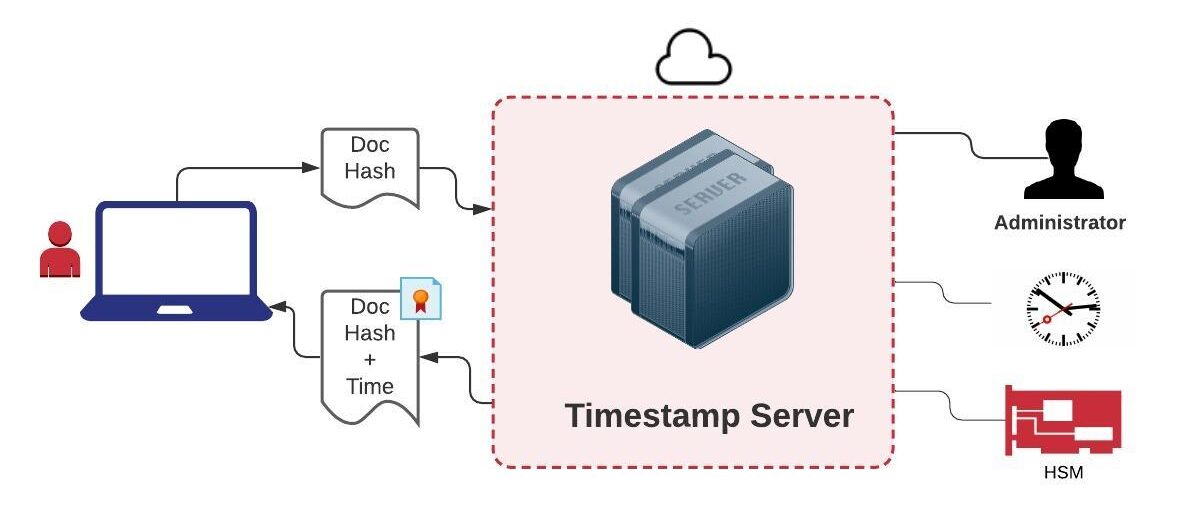
Timestamp your digital transactions with Khatim Timestamp Server
Blazing Fast, Enterprise ready, Secure, Compatible with ETSI & IETF
FAQ
Can you support signing algorithms other than RSA?
As this demo is is just for helping developers and quick testing purpose hence only RSA based signing is supported. Note that the paid version support RSA and ECDSA based signing both.
I am getting badRequest from the server what could be wrong?
Ensure your timestamp request follows RFC 3161 standard. Check your timestamp request with OpenSSL to investigate any errors. If all good send us your timestamp request and we will have a look. Check your timestamp request using the following command:
openssl ts -query -in C:\\test\\openssl\\timestamp\\tsa_request.ts -text
Can I sign powershell scripts using the free timestamp server?
Codegic free timestamp server does not support Microsoft Authenticode signing hence it is not supported.
How can I integrate with a free timestamp server?
You can communicate using any of the following ways:
- Using a timestamp client API
- Using open source tools like OpenSSL and Curl
- Integrate with off the shelf products like Microsoft Office & Adobe Acrobat
- Code signing using signtool or jar signer tools
Know more on how to integrate with a cryptographic timestamp server.
How to solve PKIX path building failure message with jarsigner?
As our timestamp server is running behind secure SSL/TLS hence so you must add the TLS certs inside your jdk\lib\security\cacerts file. This tells jarsigner tool to trust the TLS certs and ensures the secure SSL connection. You may add these certs via the standard java keytools command or use the handy Keystore Explorer. The certs to add are:
