The challenges are not limited to algorithms. They span technology, operations, ecosystems, and governance. Understanding these challenges is critical for a successful transition.
"Post-Quantum Cryptography is necessary - but it is not a simple upgrade"
PQC Lab
Evaluate & explore ML-DSA–based certificate issuance, signing and verification in a non-production environment.
Cryptographic & Algorithmic Challenges
PQC algorithms are fundamentally different from RSA and ECC. Key challenges include:
-
Higher memory usage
-
Different performance trade-offs
-
Some algorithms being stateful or complex to implement securely
Unlike mature RSA/ECC libraries, PQC implementations are still evolving.
"PQC algorithms are standardized, but large-scale operational experience is still growing"
Performance & Scalability Challenges
Larger cryptographic artifacts impact performance in unexpected ways:
Network Impact
-
Larger TLS handshakes
-
Increased latency on high-traffic systems
-
Higher bandwidth usage
Compute Impact
-
More CPU cycles for signature verification
-
Increased memory pressure
-
Potential bottlenecks in HSM-backed operations
Storage Impact
-
Faster growth of certificate databases
-
Larger logs and audit trails
-
Expanded archival storage for long-term validation
"PQC performance issues rarely appear in isolation - they cascade across systems"
PKI Infrastructure Challenges
PKI systems were designed around RSA and ECC assumptions. Challenges include:
-
CA software tightly coupled to classical algorithms
-
OCSP and CRL size growth
-
Timestamping services producing larger tokens
-
Increased load on validation endpoints
Long-lived PKI components are especially difficult to upgrade without service disruption.
"Stability and longevity are PKI’s strengths but also make migration harder"
HSM and Hardware Limitations
Many Hardware Security Modules:
-
Have limited or no PQC support
-
Are optimized for small-key RSA/ECC operations
-
May struggle with large PQC key sizes
Firmware updates, certification cycles, and vendor roadmaps further complicate adoption. Some of the leading HSM vendors like Thales, Entrust and Utimaco have provided proprietary PQC support while some of them lack PQC support with the widely adopted PKCS#11 standard.
"Migration Is a Program, Not a Patch"
Ecosystem and Compatibility Challenges
PQC requires broad ecosystem support:
-
Operating systems
-
Browsers
-
Load balancers
-
Network appliances
-
Middleware and libraries
Partial adoption creates:
-
Interoperability failures
-
Fallback risks
-
Operational complexity
As of Jan 2026, here are some of the PQC support available in software and hardware:
Operating Systems
-
Microsoft Windows & Windows Server – Microsoft announced PQC APIs and algorithm support (e.g., ML-KEM, ML-DSA) integrated into Windows Server 2025 and recent Windows 11 releases via the Cryptography API: Next Generation (CNG). Reference: https://techcommunity.microsoft.com/blog/microsoft-security-blog/post-quantum-cryptography-apis-now-generally-available-on-microsoft-platforms/4469093
-
Linux Distributions – Red Hat Enterprise Linux (RHEL) 10 and Fedora are incorporating PQC readiness with libraries like OpenSSL and GnuTLS enabling hybrid TLS algorithms; Ubuntu also sees pathways via updated cryptographic libraries. Reference: https://live.paloaltonetworks.com/t5/quantum-security-articles/the-quantum-countdown-how-hybrid-encryption-is-quietly/ta-p/1230276
Browsers
-
Google Chrome – Enabled hybrid post-quantum key agreement (e.g., X25519+Kyber) by default in recent versions. Reference: https://blog.cloudflare.com/pq-2025
-
Mozilla Firefox – Implements PQC hybrid ciphers, available in newer releases. Reference: https://developers.cloudflare.com/ssl/post-quantum-cryptography/pqc-support
-
Microsoft Edge – Inherits Chromium’s PQC support. Reference: https://developers.cloudflare.com/ssl/post-quantum-cryptography/pqc-support
-
Safari / Apple Browsers – Apple platforms are rolling out support for PQC hybrid groups in recent OS/browser updates. Reference: https://developers.cloudflare.com/ssl/post-quantum-cryptography/pqc-support
Load Balancers / Network Appliances
-
AWS Application & Network Load Balancers – Support post-quantum key exchange in TLS via hybrid PQC security policies. Reference: https://aws.amazon.com/about-aws/whats-new/2025/11/network-load-balancers-post-quantum-key-exchange-tls
-
Fortinet FortiWeb – Introduced TLS 1.3 PQC support (e.g., ML-KEM hybrid key exchange and ML-DSA signature mechanisms). Reference: https://docs.fortinet.com/document/fortiweb/8.0.3/administration-guide/426552/post-quantum-cryptography-pqc-support-8-0-3
-
Enterprise Firewalls / NGFW – Vendors like Palo Alto Networks offer PQC for management-plane TLS and hybrid post-quantum key exchange in PAN-OS. Reference: https://docs.paloaltonetworks.com/content/techdocs/en_US/whats-new/new-features/august-2025/post-quantum-ssl-support-for-pan-os-management
-
CDN / Edge Providers (Akamai, Cloudflare) – Offer PQC hybrid TLS support at the edge. Reference: https://www.akamai.com/blog/security/akamai-enables-post-quantum-cryptography-edge
Middleware & Libraries
-
OpenSSL 3.x+ – Integrated PQC (hybrid key exchange) capabilities via providers such as oqsprovider. Reference: GitHub – open-quantum-safe/oqs-provider: OpenSSL 3 provider containing post-quantum algorithms
-
BoringSSL, LibOQS – Provide PQC algorithm implementations or integration pathways for PQC. Reference: Open-Source PQC Libraries Compared: liboqs, OpenSSL 3.4, and BoringSSL Implementation Analysis – World Quantum Summit 2025
-
Rustls – Rust-native TLS stack supporting PQC hybrid key exchange. Reference: rustls-post-quantum — Rust crypto library // Lib.rs
"Crypto Is Only as Strong as Its Weakest Link"
Security & Implementation Risks
New cryptography introduces new risks:
-
Immature implementations
-
Side-channel vulnerabilities
-
Incorrect parameter selection
-
Incomplete validation logic
These risks are highest in:
-
Custom implementations
-
Embedded systems
-
Performance-optimized code paths
New Crypto ≠ Risk-Free Crypto
"PQC removes quantum risk but introduces engineering risk if poorly implemented"
Operational Reality: Migration Takes Time
Real-world PQC adoption involves:
-
Crypto inventory and discovery
-
Parallel classical + PQC operation
-
Long transition periods
-
Staff training and tooling updates
Rushed transitions increase the risk of:
-
Outages
-
Trust failures
-
Compliance violations
"PQC removes quantum risk but introduces engineering risk if poorly implemented"
What These Challenges Mean
-
PQC adoption is unavoidable
-
The transition is complex but manageable
-
Early planning reduces risk
-
Crypto agility is the most valuable capability
FAQ
Why is adopting Post-Quantum Cryptography more than just replacing algorithms?
Post-Quantum Cryptography impacts the entire cryptographic lifecycle, not just algorithms. PQC introduces significantly larger keys and signatures, which affect certificate sizes, TLS handshakes, storage, logging, HSMs, firmware, and network performance. Existing PKI systems, protocols, and applications were optimized for RSA and ECC and often assume small key sizes and fast operations. Migrating to PQC therefore requires architectural changes, crypto-agile designs, and extensive testing across infrastructure, applications, and third-party dependencies.
What are the biggest technical challenges with PQC algorithms today?
The main technical challenges include larger key and signature sizes, increased computational overhead, and ecosystem immaturity. PQC algorithms such as ML-KEM and ML-DSA increase bandwidth usage and memory requirements, which can strain constrained environments like IoT, smart cards, and embedded systems. In addition, many protocols and hardware platforms are still adapting to support PQC efficiently, and some cryptographic libraries and devices are not yet fully optimized or certified.
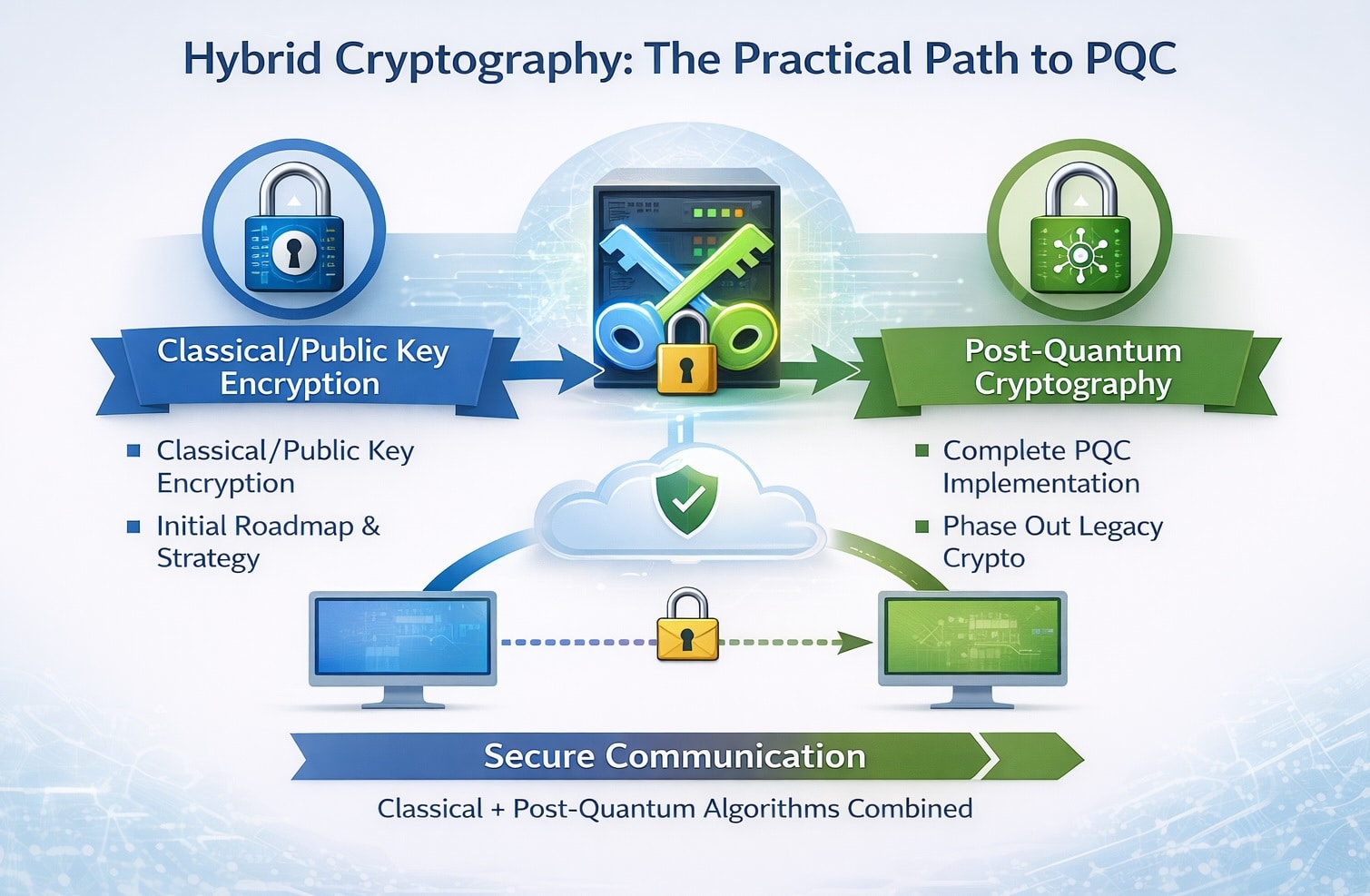
Why is hybrid cryptography considered necessary during the PQC transition?
Hybrid cryptography is necessary because PQC algorithms are still new and classical algorithms remain trusted today. A hybrid approach combines classical and post-quantum algorithms so that security holds even if one algorithm is later weakened. This approach ensures backward compatibility, reduces migration risk, and aligns with guidance from NIST, NSA, and ENISA. Hybrid deployments allow organizations to transition gradually while maintaining interoperability and compliance during the multi-year migration period.
How do legacy systems and vendors slow down PQC adoption?
Many legacy systems have cryptography hard-coded into firmware, protocols, or application logic, making algorithm replacement difficult or impossible without major upgrades. Additionally, organizations depend on vendors, cloud providers, and hardware manufacturers for PQC support. If vendors are not PQC-ready, enterprises cannot migrate critical systems independently. This creates a dependency-driven timeline, where PQC adoption must align with vendor roadmaps, software updates, and hardware refresh cycles.